TOR - The veil of Privacy And Why it isn't Broken
Dive into the privacy conscious world where none can put a face to the IP.( For the Privacy Concerned and why Tor isn't boken .... )

Tor : What is it ?
The Tor network is a group of volunteer-operated servers that allows people to improve their privacy and security on the Internet.
-torproject.org
The Onion Router
It is a network that helps individuals protect users online , by safeguarding their privacy online.It is used as an effective censorship circumvention tool and
Why Anonymity Matters
Using Tor protects you against a common form of Internet surveillance known as "traffic analysis." Traffic analysis can be used to infer who is talking to whom over a public network. Knowing the source and destination of your Internet traffic allows others to track your behavior and interests. This can impact your checkbook if, for example, an e-commerce site uses price discrimination based on your country or institution of origin. It can even threaten your job and physical safety by revealing who and where you are.
For example, if you're travelling abroad and you connect to your employer's computers to check or send mail, you can inadvertently reveal your national origin and professional affiliation to anyone observing the network, even if the connection is encrypted.
-torproject.org
It may not matter to you right now but it is a question of life and death for some people like whistleblowers, journalists, human rights activists in many countries specially in dictatorial regimes.
Open Observatory of Network Interference
Open Observatory of Network Interference
A free software, global observation network for detecting censorship, surveillance and traffic manipulation on the internet
So what outputs do we get from this :
OONI-World Statistics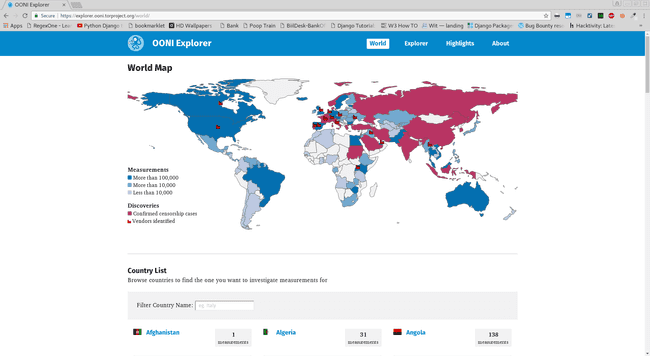
The above image shows the confirmed censorship cases and , where found the vendors who have been identified also country wise data is listed there ( go on click on the image to get enlightenment ;) ). Same goes for India :
India - OONI Statistics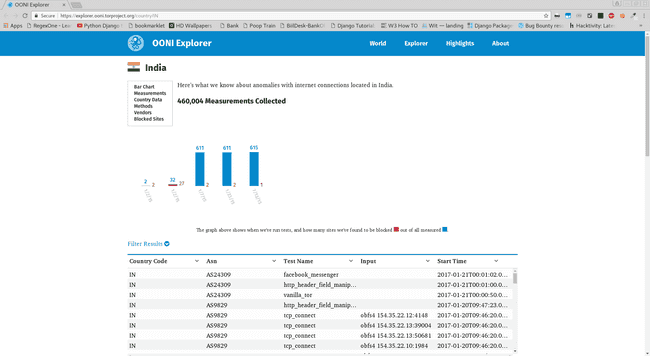
What dark magic does Tor cast
Actually its understanding of how you are being tracked with the help of technology and finding ways around it and the makers of Tor understand it fully. It protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world. Thus preventing anyone watching your Internet connection ( maybe your ISP ) from learning what sites you visit. Not just that it prevents the sites you visit from learning your physical location.
So how does it work ?
Tor Working - torproject.org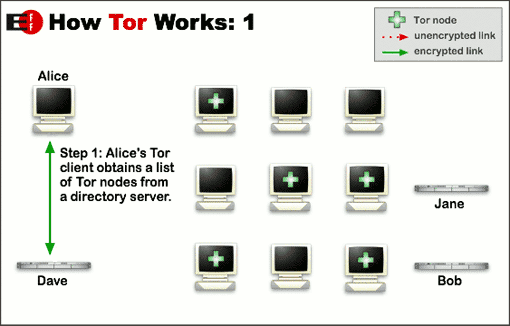
First after you have started the Tor software , the tor client , it obtains a list of tor nodes from a directory server. It is public info and thus nothing hidden in this step.
Tor Working - torproject.org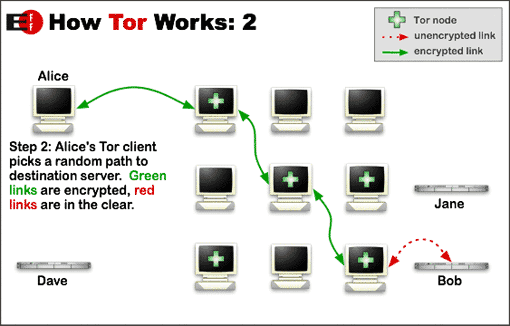
Since I have the list of all nodes so next I chose a random path to my destination server.
In the above step the tor client on the user's desktop or mobile ( yes it is for Android , named as Orbot ) builds the private network path.
To create a private network pathway with Tor, the user's software or client incrementally builds a circuit of encrypted connections through relays on the network. The circuit is extended one hop at a time, and each relay along the way knows only which relay gave it data and which relay it is giving data to.
-torproject.org
Let's understand this using an example.
Suppose I have some documents in nested box which I need to send from the person standing first in the queue to my friend standing next to the last person in queue. Now every box has a unique key, corresponding to each of the person and also has the name of the owner of the box written on it. The owners' (the people in queue ) provided me the lock corresponding to their key. Now I transfer the important document inside the box of the last person and the first person's box is the top box , second box for the second person and so on.Now imagine you are also one of those people in queue transferring my documents.
So, eventually what happens, when the box reaches you , you open your lock , see inside the box and you will find another box with a name on it for the next owner.
So what do you get , only the name of next box's owner not me and neither my friend standing next to the queue , for whom the box is destined.
Important Documents : Original Data ( In case of HTTPS traffic even the documents would be encrypted )
Boxes : Encrypted Data Packets
Lock : Public Key for encryption
Key : Private Key for decryption
My friend : The web server where data is destined for
However the last man who delivers the data to my friend can see to whom this data is being sent and what data if it's plain HTTP and not HTTPS.
Again the cycle continues for a new friend of mine or rather should I say a new website.
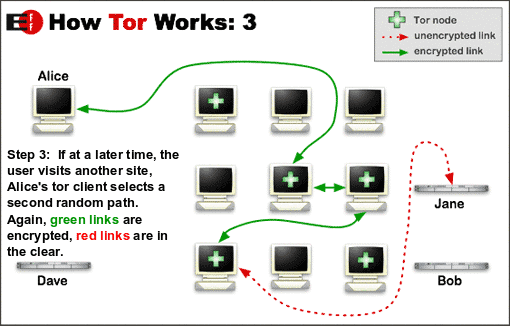
For every connection you make i.e. for every site you visit your tor client will chose a completely random path.
Some terms you would like to know:
- Entry/Guard Relay ( The first man in the queue ) - Entry point to the Tor network. Relays are selected to serve as guard relays after being around for a while, as well as having shown to be stable and having high bandwidth.1
- Middle Relay ( The people in between the queue ) - These are the middle nodes used to transport traffic from the guard relay to the exit relay. Thus preventing the guard and exit relay from knowing each other.
- Exit Relay ( The person handing the documents to my friend ) - These are exit points at the edge of the Tor network. These send traffic to the final destination intended by the client.
Statistics
As of 29th Jan 2017 :
Whole-World - Top 10 relays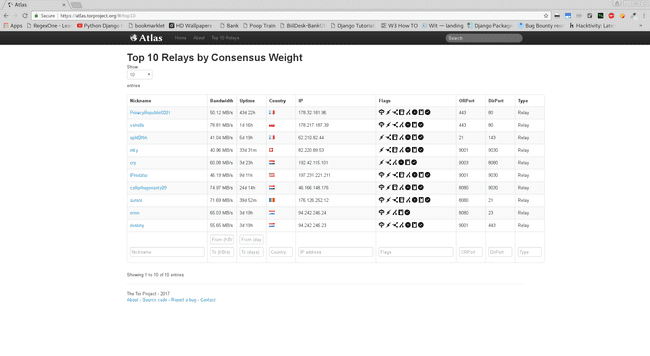
India-top-10-relays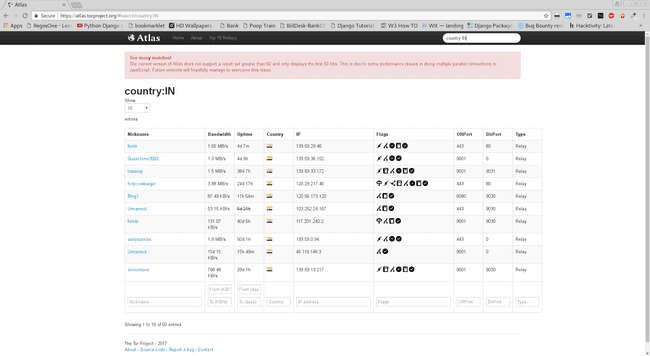
An old cartogram from University of Oxford
The Anonymous Internet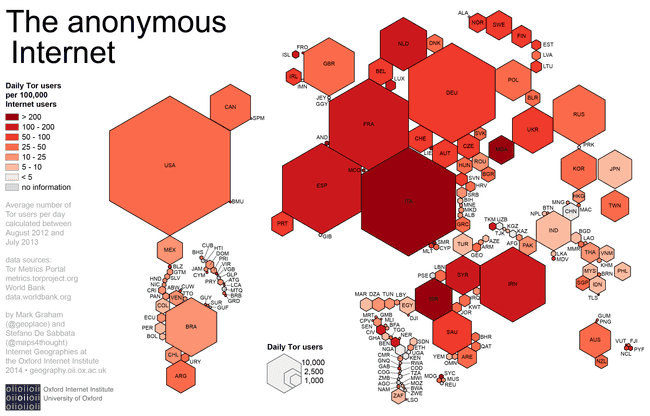
A large number of users are connecting to Tor :
UserStats Relay Country All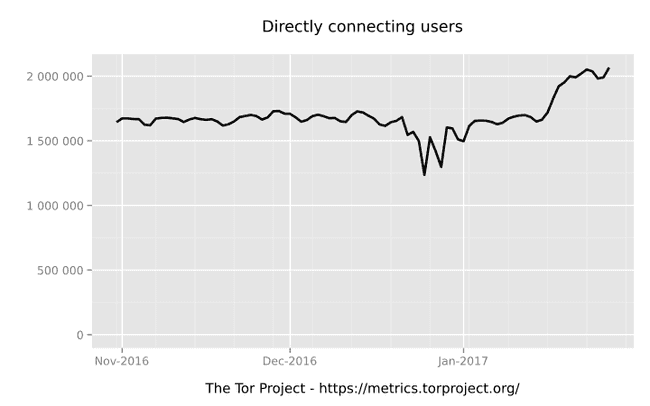
The higher the better :)
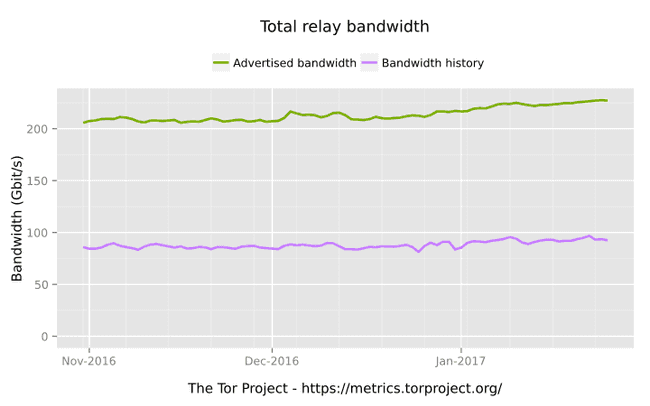
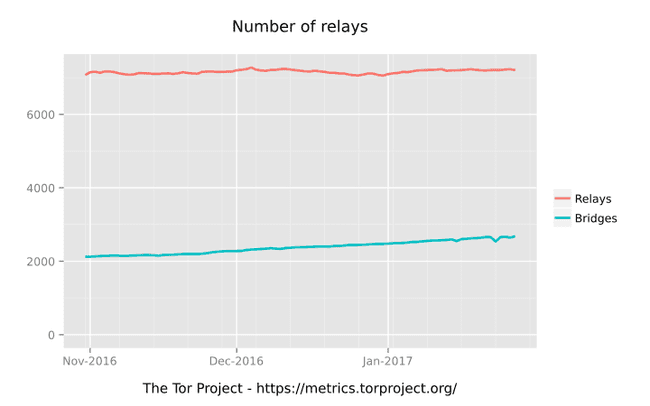
Total number of relays , these keep the anonymous network running ;)
Tor Attacks : The Truth Behind
Everyone would have heard about Edward Snowden . If not google him and thanks to him we have more insight of the capabilities of the different government agencies. Apart from that he did one more thing , actually the leaked documents did , i.e. they increased people faith in the Tor network. The summary of what is going on in the next few paragraphs is :
Tor Network was not exploited and the reason of some person being deanonymized was their bad OPSEC.
Case 1 : LulzSec /AntiSec
Case Study : LulzSec - AntiSec
What Happened : Everyone remembers LulzSec/AntiSec, scrounging the web for SQLi, DDoSing websites, dumping user databases and taking down high profile website like CIA website.
What Went Wrong : They coordinated on IRC channels and somehow the officials got to know of it and started monitoring the channel. One of the members, Sabu connected the IRC channel without using TOR, just once and bam he was caught using the packet origin. Immediately he is turned into a government informant cause he couldn't do anything , either face decades of imprisonment or dig out his workmates.
Interesting part : Jeremy Hammond was caught by logging his packet metadata from his WiFi access point ( standard wire tapping orders from the court ). Identifying his mac address to packets going to a Tor entry node and then correlating his Tor presence to his presence in the IRC channel.
Case 2 : Harvard Bomb Hoax
What Happened : A Harvard University student's attempt to escape a final exam this week by falsely reporting bomb threats against the campus in an email , claiming it to be a shrapnel bomb.
What Went Wrong : In short a lot, first it was a quick decision which lead to a lot of wrong steps.
- He used Tor to connect to guerrillamail.com , which adds X-Originating Header , thus exposing that it was from a Tor exit node
- Only using Tor for bad purposes
- Harvard Network requires to register your MAC address and they log outgoing traffic
Case 3 : Silk Road

What Happened : Silk Road , one of the most famous darknet market, it successfully operated as a Tor hidden service for over 2 years.
What Went Wrong : Numerous forum posts from same account including his real email id ,stack exchange posts asking for running tor hidden service , ordering fake id with his face on them. Apart from this , the technical details related to the capture of Robert Ulbricht is unknown .But attacks to tor hidden services is a probability but not a problem for typical user .
Conclusion:
In both of the above cases it was not the Tor network that was exploited rather it was bad OPSEC practice.
Views of Security Agencies on Tor :
TOR browser bundle makes tor user look alike :

The famous Tor Stinks presentation ( from the NSA files , leaked by **Edward Snowden **) : The Spying agencies agree that they could deanonymize a small group of Tor users but it's not trivial and not feasible in real time.
 Tor - A Low Latency Anonymity Solution](/static/326a35f2ebeed760ca9b4b912d9ae7c0/c08c5/tor-is-still-the-king.jpg)
 Tor Stinks - Proposed Ways of Deanonymizing Tor Users](/static/9501b48ec5cf6e65d534000c1063fbcf/c08c5/tor-stinks.jpg)
If the above slides are not an assurance enough then go on have a look on this :
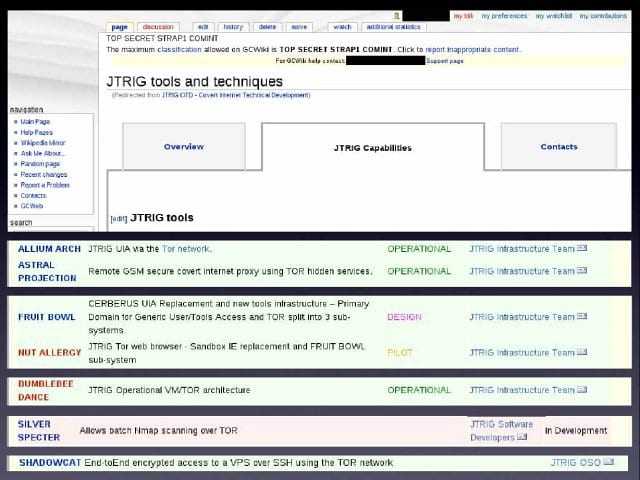
It is from the famous JTRIG Wiki , from the GCHQ spying agency , they themselves use Tor . What else assurance would you need for using Tor ??
It's not like they could be using a different Tor which is untraceable cause it is a protocol which is the same for all and as far as Tor software bundle is concerned it is free and open source i.e. anyone can make their own version however they would still need to follow the same rules of the trade.
Thus it is safe to browse Tor , use Tor judiciously and for good purposes too cause more traffic leads to more annonymity ;).
References
- DEFCON-22-Zoz-Dont-Fuck-It-Up ( Most of the images and Case Study are taken from here )
- The Tor Project
 IRC without Tor](/static/4885dcc54bf7e3e807a934aeffba815d/c08c5/irc-without-tor.jpg)
 Case Study : Harvard Bomb Hoax](/static/15570649fe6cf82ced87b5f29ba429f1/c08c5/case-study-harvard-bomb-hoax.jpg)
