bcrypt - Future proof hashing
Breaking bcrypt hash using Hashcat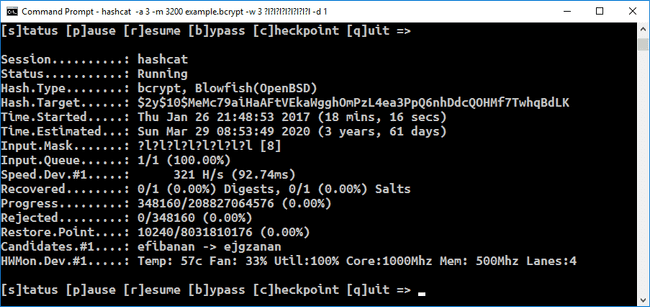
bcrypt is a password-hashing function designed by Niels Provos and David Mazières, based on the Blowfish cipher and presented at USENIX in 1999.
What's interesting about bcrypt ?
Besides incorporating a salt to protect against rainbow table attacks, bcrypt is an adaptive function: over time, the iteration count can be increased to make it slower, so it remains resistant to brute-force search attacks even with increasing computation power.
Thus making it future proof.
The bcrypt function is the default password hash algorithm for OpenBSD and other systems including some Linux distributions such as SUSE Linux.
A bcrypt hash string is of the form:
$2b$[cost]$[22 character salt][31 character hash]
For example:
$2a$10$N9qo8uLOickgx2ZMRZoMyeIjZAgcfl7p92ldGxad68LJZdL17lhWy
\__/\/ \____________________/\_____________________________/
Alg Cost Salt HashWhere:
$2a$: The hash algorithm identifier (bcrypt)10: Cost factor (210 ==> 1,024 rounds)N9qo8uLOickgx2ZMRZoMye: 16-byte (128-bit) salt, base64-encoded to 22 charactersIjZAgcfl7p92ldGxad68LJZdL17lhWy: 24-byte (192-bit) hash, base64-encoded to 31 characters
Source : bcrypt - Wikipedia
Pic Credits : Is 'aqenbpuu' a bad password?
