Making of a BOTNET
So are ready to know as to what it takes for setting up a botnet...
What is a Botnet (Seriously ??) ?
Botnet Explained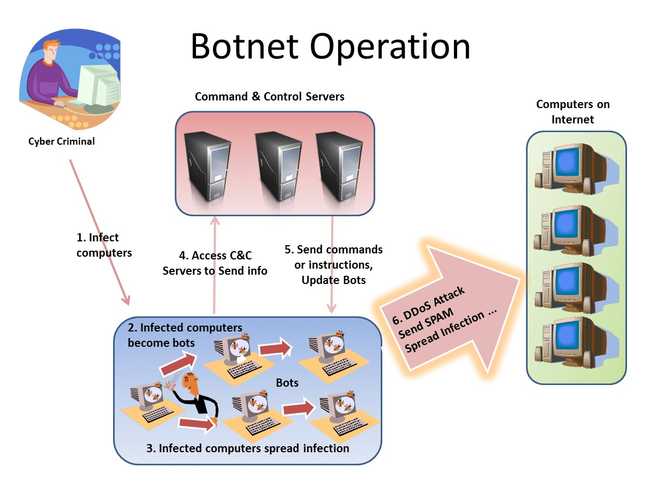
Simply put , botnet is a network of computers , usually malware affected and remotely controlled by a C2C a.k.a Command and Control server. Whoever controls the server can do whatever with the bots they control.
Just to give an insight of the commands1 , bots like Zeus can execute on the victim are :
- Reboot – Reboot the computer
- Kos – Delete system files, killing the computer
- Shutdown – Shutdown the computer
- Block_url – Disable access to a particular URL
- Unblock_url – Restore access to a particular URL
- Block_fake – Do not inject rogue HTML into pages matching a defined URL
- Unlock_url – Re-enable injection of rogue HTML to pages matching defined URL
- Rexec – Download and execute a file
- Lexec – Execute a local file
- Lexeci – Execute a local file using the interactive user
- Addsf – Adds a file mask for local search
- Delsf – Removes file mask for local search
- Getfile – Upload a file or folder
- Getcerts – Steal digital certificates
- Resetgrab – Steal information from the PSTORE (protected storage) and cookies
- Upcfg – Update configuration file
- Rename_bot – Rename bot executable
- **Bc_del ** – Delete a back door connection
- Bc_add – Initiate back door by back-connecting to a server and allow arbitrary command execution via the command shell
P.S. : Source code of Zeus has been leaked and available to download and modify.
Mechanism
The botnet works in quite a simple fashion. You download a software (malicious) from some 3rd party website , assuming it to be a cracked version of the paid game or software , you are dying to use. As soon you click the executable the malware starts its work and connects back to it’s C2C server and registers you as the new bot with a unique id.
After the server uniquely identifies the bot , the bot starts a stream of data , so as to say . And all your data ( such as banking details or photos on local hard drive or blueprints of a project , anything and everything), credentials belong to the bot owner.
The bot may also spread like , the one in image 'SPYEYE', used one of the publicly available exploits , Microsoft RDP exploit . However there can be many other mechanisms like cracked softwares/games , torrents, Hacking software etc.
Persistence : What is a bot if it isn’t persistent over multiple restarts.The following list of registry keys are accessed during system start in order of their use by the different windows components:2
1) HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\BootExecute
2) HKLM\System\CurrentControlSet\Services (start value of 0 indicates kernel drivers, which load before kernel initiation)
3) HKLM\System\CurrentControlSet\Services (start value of 2, auto-start and 3, manual start via SCM)
4) HKLM\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
5) HKCU\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
6) HKLM\Software\Microsoft\Windows\CurrentVersion\RunServices
7) HKCU\Software\Microsoft\Windows\CurrentVersion\RunServices
8) HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify
9) HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit
10) HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\\Shell
11) HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\\Shell
12) HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\ShellServiceObjectDelayLoad
13) HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce
14) HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnceEx
15) HKLM\Software\Microsoft\Windows\CurrentVersion\Run
16) HKCU\Software\Microsoft\Windows\CurrentVersion\Run
17) HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce
18) HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
19) HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
20) HKCU\Software\Microsoft\Windows NT\CurrentVersion\Windows\load
21) HKLM\Software\Microsoft\Windows NT\CurrentVersion\Windows
22) HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SharedTaskScheduler (XP, NT, W2k only)
23) HKLM\Software\Microsoft\Windows NT\CurrentVersion\Windows\\AppInit_DLLsThe software path mentioned in these keys are run during startup.So there is ample space for the malware to slip into one of these and remain persistent. You can check out the currently configured autorun softwares using 'Autoruns' a windows sysinternals tool.
What next : The bot owner owns your virtual life as long as the PC in context is used.
They can use your PC for malicious activities , such as DDoS and thus implicating you. Also your PC can be used for hosting content which even you won’t be aware of. It can also be used as a proxy server.
The image of a botnet toolkit named 'SPYEYE' | Image Courtesy : WebRoot Blog The image of a botnet toolkit named 'SPYEYE'](/static/b4bb6b47acfa6855d10d272b68b24d80/a6d36/spynet_botnet_toolkit.png)
Value of a hacked PC | Image Courtesy : KrebsOnSecurity hackedpc2012](/static/c1f5e9ece06af2c9bf74425245229d1c/a6d36/hackedpc2012.png)
What it takes ...
Actually dedication , if not money ( Yes you can buy your own botnet ).
The going rate as mentioned here is :
| GeoPolitical Area | 1,000 Bots | 5,000 Bots | 10,000 Bots |
| World Mix | $25 | $110 | $200 |
| Confirmed EU | $50 | $225 | $400 |
| Canada, GB, Germany | $80 | $350 | $600 |
| USA | $120 | $550 | $1,000 |
Tech stack of a botnet
- BulletProof Server, a really secure server. Most certainly purchased through Bitcoins.
- If you can code then your own, malware, like mine else there are many malware samples available to download and create a botnet.
But wait weren’t we talking of making our own botnet…
So what if I don’t have bitcoins and so no bulletproof hosting, am I doomed ?
Actually this is the category in which most of us belong and since you are reading this with the sole intention of creating the next greatest botnet (or even if you aren’t ) I won’t disappoint you.
The malware I wrote will come to your rescue . Even though it is naive but it was written with the sole purpose of experimenting with the idea of free web hosting servers to be used as C2C server.
How to setup the python malware :
The Github Link .
Features :
- 2 Way interaction without public IP ( without public IP ) : Upto some extent using the
rtc.phpfile as mediator ( ToDo : Implement database for commands specific to a particular bot ) - Can work on any free webhosting service provider, (check the list )**
- PHP script can automatically create folders based on the unique
botIdcreated and sent by the bot - Persistent ( otherwise what use it is as bot )
-
Send identification details such as :
- MAC address
- Locale ( such as en-IN or en-US )
- Public IP
- Platform (x86 or x86_64)
- Architecture
- Node Name in the network
-
Multi threaded Implementation for :
- Sending the loot
- Keylogger ( so that we don't miss that important key )
- Receiving Command
- Sends MD5 hash of the file , before uploading the original file so as to check for any bad upload
- Retries until the file is uploaded ( which is checked using the checksum sent earlier )
- Screenshots : Takes screenshots based on the URL of the webpage ( this needs to be polished )
- Search command on the Bot side to search for the files
- CMD commands can be executed by the bot
The main file is the Client.py, which needs to be compiled and run on the victim machine, it has been tested on my PC and works out to be fine.
Disclaimer
Any actions and or activities related to the material contained within this website is solely your responsibility.The misuse of the information in this website can result in criminal charges brought against the persons in question. The author will not be held responsible in the event any criminal charges be brought against any individuals misusing the information on this website to break the law.
This site may contain links to materials that can be potentially damaging or dangerous.
